How to Apply the NIST Risk Management Framework: A Comprehensive Guide to Effective Risk Management

In today's rapidly evolving digital landscape, organizations face an ever-increasing array of risks that can threaten their operations, reputation, and financial stability. To effectively navigate these challenges, a comprehensive risk management framework is essential. The National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) provides a proven and widely acknowledged approach to managing risk in information systems and organizations. 4 out of 5 This in-depth guide will delve into the NIST RMF, equipping you with a thorough understanding of its principles, processes, and best practices. We will explore how to apply the framework in your organization, enabling you to identify, assess, and mitigate risks effectively. By leveraging the NIST RMF, you can enhance cybersecurity, ensure organizational resilience, and gain a competitive edge in the face of evolving threats. The NIST RMF is a comprehensive framework that provides guidance on risk management for information systems and organizations. It consists of seven steps, each focusing on a critical aspect of risk management: The NIST RMF is designed to be flexible and adaptable, allowing organizations to tailor it to their specific needs and environments. It promotes a holistic approach to risk management, considering both cybersecurity and organizational risks. By following the RMF's systematic steps, organizations can establish a robust risk management program that protects their critical assets and ensures business continuity. To effectively apply the NIST RMF in your organization, it is crucial to follow each step meticulously. Here's a step-by-step guide to help you navigate the framework: Begin by defining the scope of your risk assessment and identifying the stakeholders involved. Establish a risk management team and develop a risk management plan. Identify and prioritize the risks to your organization's information systems and assets. Assess the likelihood and impact of each risk using qualitative or quantitative methods. Based on the risk assessment, select and implement appropriate security controls to mitigate identified risks. These controls can include technical, administrative, and physical measures. Put the chosen security controls into practice. This involves configuring systems, implementing procedures, and providing training to employees. Evaluate the effectiveness of the implemented security controls. Conduct periodic assessments to ensure they are operating as intended and meeting the desired security objectives. After the security controls have been assessed and deemed effective, the system can be authorized for use. This involves obtaining approval from appropriate authorities and documenting the authorization decision. Continuously monitor the system to detect any changes or vulnerabilities that may impact its security posture. Conduct regular risk assessments and make necessary adjustments to the risk management program as needed. Implementing the NIST RMF offers numerous benefits for organizations, including: The NIST Risk Management Framework provides organizations with a powerful tool to manage risk effectively. By following the framework's systematic approach, organizations can identify, assess, and mitigate risks to their information systems and assets. This comprehensive guide has provided a roadmap for implementing the NIST RMF, empowering you to enhance cybersecurity, ensure organizational resilience, and gain a competitive edge in the face of evolving threats. Embark on your risk management journey today and unlock the benefits of the NIST RMF. By embracing a proactive approach to risk management, you can build a more secure and resilient organization, ensuring business continuity and success in the years to come. Empowering Organizations with Effective Risk Management
Language : English File size : 750 KB Text-to-Speech : Enabled Screen Reader : Supported Enhanced typesetting : Enabled Print length : 112 pages Lending : Enabled Demystifying the NIST Risk Management Framework
Implementing the NIST RMF: A Step-by-Step Guide
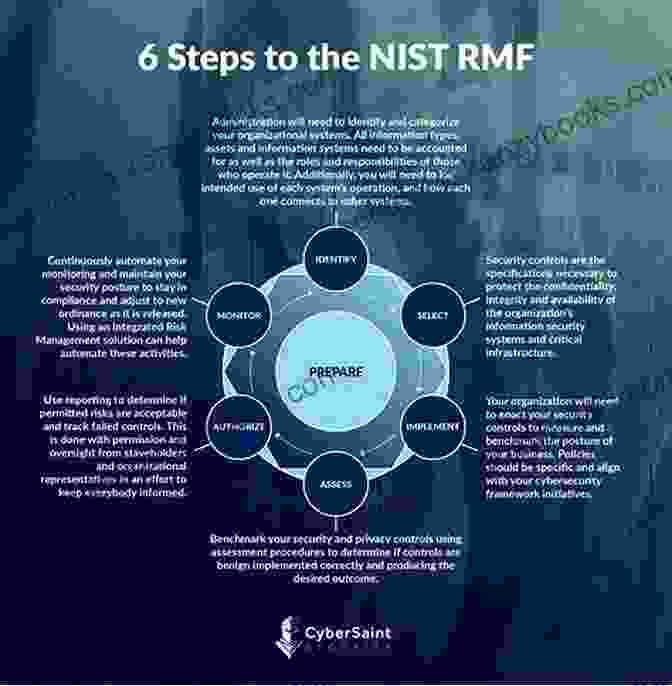
Step 1: Prepare for Risk Assessment
Step 2: Conduct Risk Assessment
Step 3: Develop Security Controls
Step 4: Implement Security Controls
Step 5: Assess Security Controls
Step 6: Authorize System
Step 7: Monitor System
Reaping the Rewards of NIST RMF Implementation
Empowering Organizations through Effective Risk Management
Take the Next Step Towards Risk Management Excellence
If you are ready to elevate your risk management practices, we invite you to explore our comprehensive online course on the NIST Risk Management Framework. Our expert instructors will guide you through the intricacies of the framework, providing hands-on guidance and practical insights.
Enroll today and empower your organization with the knowledge and tools to navigate the risk landscape confidently. Together, we can build a more secure and resilient future for your business.
4 out of 5
| Language | : | English |
| File size | : | 750 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 112 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Joanne Edmund
Joanne Edmund John E Sarno
John E Sarno Jim Dwyer
Jim Dwyer John E Finn
John E Finn Pascal Baudar
Pascal Baudar John F Carafoli
John F Carafoli Jim Atwell
Jim Atwell Samantha Michaels
Samantha Michaels John Giordano
John Giordano Sadie Gardner
Sadie Gardner Jim Dekorne
Jim Dekorne John Douillard
John Douillard John Loupos
John Loupos John Heinrichs
John Heinrichs Jodie Sarginson
Jodie Sarginson Joanna Penn
Joanna Penn Joyce Meyer
Joyce Meyer Simon Rush
Simon Rush John Gray
John Gray Katie Bishop
Katie Bishop
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
 Marvin HayesUnlock the Power of Tumblr: A Comprehensive Guide to Marketing Your Business...
Marvin HayesUnlock the Power of Tumblr: A Comprehensive Guide to Marketing Your Business...
 Gregory WoodsThe Vanishing Doorknob Haynes: An Enchanting Tale that Unlocks a World of...
Gregory WoodsThe Vanishing Doorknob Haynes: An Enchanting Tale that Unlocks a World of... Nikolai GogolFollow ·6.9k
Nikolai GogolFollow ·6.9k Liam WardFollow ·8.8k
Liam WardFollow ·8.8k Herman MelvilleFollow ·18.9k
Herman MelvilleFollow ·18.9k Juan RulfoFollow ·11.7k
Juan RulfoFollow ·11.7k Norman ButlerFollow ·4.2k
Norman ButlerFollow ·4.2k Ed CooperFollow ·19.4k
Ed CooperFollow ·19.4k Stanley BellFollow ·6.8k
Stanley BellFollow ·6.8k Cody RussellFollow ·7.5k
Cody RussellFollow ·7.5k

 Dustin Richardson
Dustin RichardsonHero Heart, Noble Heart: A Literary Odyssey of Courage...
Immerse Yourself in an Extraordinary...

 Jerry Ward
Jerry WardDaily Fire Devotional: 365 Days In God's Word
Embark on a transformative spiritual journey...

 Chris Coleman
Chris ColemanEveryone Gets to Play: Discover the Revolutionary Power...
Are you ready to experience the healing power...

 Gil Turner
Gil TurnerUnlock Your Health Potential: An Exploration of WebMD...
In the labyrinthine...
4 out of 5
| Language | : | English |
| File size | : | 750 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 112 pages |
| Lending | : | Enabled |